The first cryptocurrency was created with good intentions and is a great technology for secure, decentralized, private payments. However, as in any field, the cryptocurrency sector has become a popular place for many scammers. In fact, a large number of scammers is a dark side of cryptocurrency anonymity.
In this article, we will analyze the most common types of scams in the crypto industry. These are fraudulent tricks that you need to be able to recognize and avoid. Be careful, and then working with digital assets will only bring benefits. Let’s get started!
#1 Fake Wallets
We always recommend using non-custodial wallets that do not store user keys and seed phrases on their services. Still, this does not mean that they are 100% protected from hacking.
Let’s take a Metamask wallet as an example. It is one of the most popular services for storing ETH, ERC-20 tokens, and other assets, as well as connecting to dApps. Therefore, scammers usually disguise themselves as official Metamask app.
The developers are aware of the problem and make the following recommendations:
-
- Do not store your recovery passphrase on your PC since it can be compromised by malware.
-
- Do not visit suspicious sites by following unknown links.
-
- Never share your keys or recovery phrases with anyone. Official wallets and exchanges do not request them, and this is done exclusively by attackers.
-
- Do not give dApps and smart contracts unlimited access to the use of funds. Sometimes they do this for the sake of convenience so as not to confirm the transaction each time. But this is not safe: attackers can hack the app and withdraw all funds.
-
- Choose your app or extension carefully, so you don’t install a fake one. To do this, follow the download links only from the official website. The same goes for other wallets.
A non-custodial wallet means that the developers will not be able to return the stolen funds in any way. This is technically impossible since they do not have access to your keys and transactions. That is why it is extremely important to be careful. If you have lost only part of the money, immediately create a new wallet and transfer the rest to it. Write down a seed phrase on paper and store it offline.
#2 Fake ICOs
ICO is an initial coin offering. It’s one of the most popular seed funding methods among cryptocurrency startups. This is similar to IPOs in traditional finance, with the difference that IPOs tend to be used by long-established and well-established companies, while ICOs tend to be young and risky. Some ICOs brought huge profits to investors, but many turned out to be scams.
Types of ICO scams:
-
- Exit Scam. The most foolish and clumsy fraudulent operation — creators raised funds and suddenly disappeared without leaving any information to investors. In 2018, it was reported that almost $100 million contributed to ICOs was stolen through an exit scam.
-
- Bounty Scam. The bounty program should pay rewards to users who help promote and advertise the project in the early stages or look for vulnerabilities in it. In the event of a bounty scam, the promised reward is not paid.
-
- Exchange Scam. Developers launch ICO (IEO) on a fake crypto exchange to mislead investors.
-
- White Paper Plagiarism Scam. It’s plagiarism of white paper, the main technical document of a project. The text is copied from any other project, and then the name is simply replaced everywhere.
-
- URL Scam. It’s all about creating fake websites that imitate a real honest ICO and specifying your own crypto wallets for depositing coins. Due to inattention, many users send money to such wallets.
To avoid participating in such projects, follow a few rules. Always read a white paper. The document should indicate the goals and ways to achieve them, a financial model, analytics, and implementation timelines. Evaluate the promises and how realistic they are.
#3 Social Network Scams
One type of hack that is not at all unique to the blockchain industry is an attack on the social networks of projects and posting false information there. For example, at the end of April 2022, the hacking of the Bored Ape Yacht Club Instagram account cost investors $3 million.
Scammers posted a link to a fake website where users connected their wallets to launch NFTs (as they thought). In fact, in this way, they allowed their funds to be stolen.
Twitter is well known for issues such as spambots and fake accounts of famous people. According to the Federal Trade Commission, within 7 months in 2020-2021, about $2 million was stolen with the help of fraudsters who own fake Elon Musk accounts. Musk himself, who recently bought Twitter, said he would fight spambots and fake accounts.
#4 Fake Exchanges
One of the most common types of fraud is the launch of fake trading platforms that imitate real exchanges.
For example, you might receive the following fake message (supposedly from the PancakeSwap exchange):
Crypto Giveaway: Claim free 45 CAKE on your PancakeSwap wallet! Claim your giveaway via the link below!
The link in this message has a typo, and you should never follow it, let alone confirm any transactions.
And a Binance exchange in May 2022, shortly after entering the Turkish market, warned users about fake banner ads in Istanbul and other cities. Attackers posted a fake ad for Binance and indicated the number that scammers answer when users call. Those who call are fed false promises in exchange for their data, such as seed phrases from personal crypto wallets.
#5 Mining Scams
Here is a story that broke a few weeks ago. The US Department of Justice charged the senior executive of Mining Capital Coin with a $62 million crypto investment scam. According to the allegation, Luiz Capuci Jr. and his accomplices deceived investors about the potential for profit from mining contracts and their own Capital Coin token, which was allegedly backed by ‘the largest cryptocurrency mining farm.’
In the case of cloud mining, it’s very difficult, and often impossible, for an ordinary user to check whether a company really has the capacities that it offers to buy or it’s just a Ponzi scheme.
Capuci has sold mining packages to at least 65,000 investors since January 2018, offering a 1% daily return. How can you guarantee profitability in a business like mining? Moreover, 1% per day (30% per month) is more like an HYIP than a legal investment.
The Ministry of Justice claims that instead of using investors’ money to mine cryptocurrencies, Capuci transferred them to his own crypto wallets and spent them on luxury goods — yachts, cars, and real estate. If found guilty on all charges, he faces up to 45 years in prison.
#6 Fake Support Services
You should contact the technical support of an exchange you use directly from the official website through a special form or by email indicated on the website.
If you ask questions on social networks, there is a risk that scammers will text you and introduce themselves as technical support managers. Under this pretext, they may request data from your wallet, account login/password, or other confidential information.
Such situations occur not only in the crypto sphere but also in almost any other sector. It’s doubtful that technical support will write to users in PM in social networks. On the contrary, most likely, they will ask you to create a ticket on a site.
#7 Pyramid (Ponzi) Schemes
Cryptocurrency is often called a pyramid or Ponzi scheme by newbies who don’t understand the essence of mining and decentralization.
However, there are indeed a large number of projects in the field that use this illegal method. Still, crypto is used here solely because of its anonymity compared to traditional assets. Organizers break the law, and they know it very well. Therefore, they do not need to disclose the data of their cards and digital wallets.
A Ponzi scheme is an investment scam that pays out profits to existing investors from funds contributed by new investors.
Organizers often attract new people with the promise of investing in opportunities that are said to bring high returns with minimal risk.
How to recognize a pyramid scheme:
-
- High returns with little or no risk.
-
- Overly stable returns. Every investor knows that profit can rise and fall, and it cannot give exactly the same percentage from month to month.
-
- Lack of official registration and state licenses.
-
- Complex secret strategies and structures. It’s better to avoid schemes that are difficult to understand or don’t provide complete information.
-
- No requirements for investors. Standard lures are the following: ’a student, a pensioner, a mother on maternity leave can earn money with us, and employment is 2-3 hours a day with a yield of 30% per month.’ Free cheese happens only in a mousetrap.
-
- Difficulties with getting payments. If you are already participating in a project where payouts are very infrequent, give it up as soon as possible since the pyramid is about to collapse.
#8 Pump&Dump
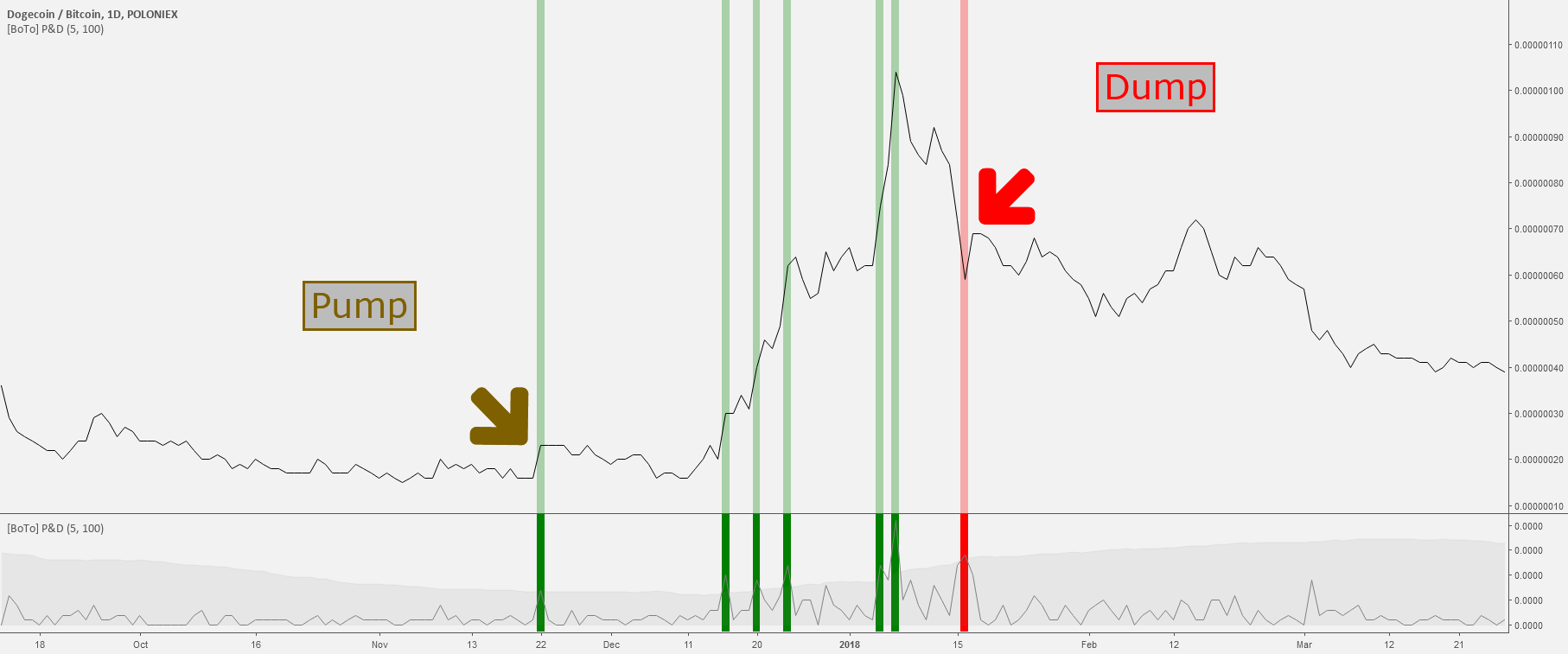
A pump and dump scheme exists in all investment areas, but it has become widespread in the crypto sphere due to the novelty and popularity of digital assets. The bottom line is that holders of a low-value asset are promoting and discussing it to encourage others to buy a token and increase its price.
In this regard, it’s necessary to mention telegram channels with investment tips, where tokens are often pumped. And when thousands of people buy, and the price reaches a certain point, a dump follows. As a result, late investors are left with nothing.
#9 Phishing Attacks
As a form of fraud, phishing has been used long before the cryptocurrency industry since the mid-90s. The main purpose of such an attack is to deceive inexperienced users into voluntarily handing over their data or money.
Let’s consider the main types of phishing attacks:
Spear phishing. A report by data protection firm Barracuda Networks has confirmed the growing prevalence of attacks in which attackers target specific people with fake emails purporting to be from a legitimate sender. Typically, the goal is for a user to reveal sensitive information or navigate to a malicious website. Check sender links and email addresses carefully, avoid public Wi-Fi networks, and always enable two-factor authentication where possible.
DNS hijacking. Hackers replace known websites with a malicious interface, tricking users into entering their data on a fraudulent domain. This type of attack is more technically difficult. Various projects regularly become victims of such an attack. One of the most effective ways to protect against a DNS attack is to use a VPN. Also, make sure to check if a certificate is valid on the site you are using.
Understanding phishing attacks is one of the important steps to protecting your crypto assets. This type of scam is classified as a non-trading risk, and it is entirely within your power to protect yourself from it. Everything is much more complicated with trading, but that’s a completely different story.
#10 Malicious Software
One of the main examples of malware associated with cryptocurrencies is hidden miners.
The first malware that mined Dogecoin using the Odyssey computer cluster at Harvard University was discovered in 2014. In the same year, illegal BTC mining using National Science Foundation (NSF) supercomputers was uncovered.
In 2017, such software hit the headlines because it became mainstream. Cybercriminals have used every effort to take possession of insufficiently protected computers, servers, and browsers and receive cryptocurrency in their wallets.
Two main methods of hidden mining:
-
- Hackers inject malicious code into a victim’s PC (for example, via a link). The script runs in the background every time the computer is turned on.
-
- Cybercriminals inject a script into a website. When a victim visits the site, mining starts from their computer. Detecting such software is very difficult because it is not stored on computers.
Regardless of the method used, the code solves math problems on victims’ PCs and sends the solutions to a hacker-controlled server. As a result, they receive mining rewards.
Other malicious programs include those that intercept the addresses, passwords, and other data you enter, as well as those that replace a crypto address in a clipboard with an address of scammers.
The main way to protect yourself is to purchase a good quality antivirus/firewall and also not to click on suspicious links from unknown sources.
Conclusion
To avoid most cryptocurrency scams, you should never turn off your caution and some suspicion. Every mail or SMS you receive without your request should be considered fraudulent. Each project or investment scheme in which you are offered to invest money should be carefully and comprehensively studied for value, prospects, and technical solutions. Make sure to bookmark the trusted exchanges you use. Install a reliable antivirus and keep its databases updated regularly.
Have you ever become a victim of scam attacks? Feel free to share your experience in the comments below!

Leave a Reply